Crypto Key Generate Modulus 1024 Cisco Switch
Cod4 key code generator 2015. Apr 13, 2018 COD4 multiplayer Key Code Generator is unique and best program for all players who want free game. Mar 02, 2015 This video contains Call of duty multiplayer gaming with a valid settings and a keycode. Guys please like our facebook page for further updates https://www.f. May 26, 2015 Call Of Duty Ghost Keygen Free Download No Survey PC PS3 Xbox - Call Of Duty Ghost Key Generator. May 16, 2015 can i get an url from where i can download the complete setup for COD4. Cause after installing and providing the cd key when i start the game it. Feb 22, 2016 Call of duty 4 multipalyer gaming with key code - Duration: 1:23. Tech Infinity 114,322 views.
- How I create RSA key and enable SSH access in Cisco VG202, in a Cisco router I use the next commands(but in a VG not exists): conf t crypto key generate rsa modulus 1024 ip domain-name domain-name ip ssh version 2 ip ssh time-out 120 ip ssh authentication-retries 3 line vty 0 4 transport input telne.
- Crypto key generate rsa general-keys modulus 2048. But I'm still seeing a 1024 key, anyone know why this is? Version 2.0 Authentication timeout: 120 secs; Authentication retries: 3. Minimum expected Diffie Hellman key size: 1024 bits. IOS Keys in SECSH format(ssh-rsa, base64 encoded). About to test the fiber with Cisco switches to make.
- First, you must create the keys on both devices. We recommend using at least 1024-bit keys in production networks: Router1#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Router1(config)#crypto key generate rsa The name for the keys will be: Router1.oreilly.com Choose the size of the key modulus in the range of 360 to 2048 for your General Purpose Keys.
- Crypto Key Generate Modulus 1024 Cisco Switch For Windows 10
- Crypto Key Generate Modulus 1024 Cisco Switch Key
Step 1: Inspect your hardware
Dec 12, 2017 Re: crypto key generate rsa please define a hostname other than switch when you have added the domain name as Julio stated and you go to create the keys again the default will be 512, type 1024 and hit return so it only uses ssh v2 as v1 is unsecure and can be hacked and its advised to not use it anymore where possible. I did a little research and found out that if I removed the rsa key by using this command ' crypto key zeroize rsa' and then added the 'crypto key generate rsa generate-keys modulus 1024, then that would work. Any thoughts? No service pad. No service password-encryption. Hostname Sales-SW-ACC2. Ip domain name my.company.come. Oct 02, 2015 SSH Config and crypto key generate RSA command. Use this command to generate RSA key pairs for your Cisco device (such as a router). Keys are generated in pairs–one public RSA key and one private RSA key. If your router already has RSA keys when you issue this command, you will be warned and prompted to replace the existing keys with new keys.
Check the model number of your shiny new switch. Or, if you are using a spare, check the device hardware and its connected cables for any damages. If everything checks out, power on the switch and verify that all the indicator lights are in working order. Next, use a rollover cable to console into the switch from your computer. To do this, you will need to download and install Putty (or a similar, fun-named software tool). Run Putty and select the 9600 speed serial connection. You are now connected to the switch and ready to check the output of the following commands:
- show version
- show running-config
- show VLAN brief
- show VTP status
- (config)# IP domain-name routerfreak.com
- (config)# hostname Switch01
- (config)# interface VLAN1
- (config)# description Management VLAN
- (config)# IP address 192.168.101.1 255.255.255.0
- vtp [client server transparent]
- vtp domain name
- description *** DESCRIPTION ***
- switchport access vlan ###
- sswitchport mode access
- power inline consumption ###
- queue-set 2
- mls qos trust dscp
- storm-control multicast level 50.00
- no cdp enable
- spanning-tree portfast
- spanning-tree bpduguard enable
- Interface GigabitEthernet1/0/1
- description *** UPLINK ***
- switchport trunk encapsulation dot1q
- switchport mode trunk
- speed 1000
- duplex full
- Switch01(config)# crypto key generate rsa
- The name for the keys will be:
- Switch01.routerfreak.com
- How many bits in the modulus [512]: 1024
- % Generating 1024 bit RSA keys, keys will be non-exportable..[OK]
- # line vty 0 4
- (config-line)# transport input ssh
- (config-line)# login local
- (config-line)# password routerfreak
- (config-line)# exit
- # line console 0
- (config-line)# logging synchronous
- (config-line)# login local
- Switch01# service password-encryption
- remote-computer# ssh 192.168.101.1
- Log in as: username
- Password:
- Switch01>en
- Password:
- Switch01#
For spare switches, make sure to delete the flash:vlan.dat file to erase the previous configuration.
Step 2: Set up management IP
Unlike with that punny name you gave your home Wi-Fi network, when setting up the hostname for your switch you should probably stick to a more professional and standard naming convention. Follow any preset naming assignment your company is using and then assign an IP address on the management VLAN. Next, make sure your switch has a set hostname and domain name:
Step 3: Check VTP revision number
Hit the show vtp status command to reveal your Virtual Trunking Protocol (VTP) revision numbers. The VTP revision numbers determine which updates are to be used in a VTP domain. When you set a VTP domain name, the revision number is set to zero—after which each change to the VLAN database increases the revision number by one. Your switch will only process data from a neighboring switch coming from the same domain and if the revision number of the neighboring switch is higher than its own. This means that the switches will update their VLAN configuration based on the VTP information being sent by the switch with the highest revision number.
So, before you add your switch to the network, you’re going to want to set its revision number to zero. To easily reset the domain back to zero, change the config mode to transparent:
Step 4: Configure access ports
You might already have a template ready for access port configuration, but in case you don’t, here are some commands you should use:
Step 5: Configure trunk ports
Enter the command sh int g0/1 capabilities and check the trunking protocol supported. If ISL is supported, you have to issue the switchport trunk encapsulation dot1q on the trunk port configuration. If not, simply type switchport mode trunk. It means there is no other encapsulation supported so there is no need for an encapsulation command. It only supports 802.1Q.
Step 6: Configure access ports
After already performing basic network switch configurations, it’s time to generate RSA keys to be used during the SSH process, using the crypto commands shown here:
Choose the size of the key modulus in the range of 360 to 2048 for your General Purpose Keys. Choosing a key modulus greater than 512 may take a few minutes.
Step 7: Set up VTY line config
If you have not set the console line yet, you can easily input these values:
Set the enable password using the enable secret password command. Then, set the privilege exec password with username name privilege 15 secret password. Make sure that the password-encryption service is activated.
Verify SSH access by typing ‘sh ip ssh’ to confirm that the SSH is enabled. You can now try to log in from a remote machine to verify that you can ssh to your Cisco switch.
Finishing touches
You’ve made it through the learning process with (hopefully) minimum bumps and bruises, and you’re just about ready to ride off. All that’s left is to test your access, reload the switch, and ready the cables. Once that’s done, label your switch, rack it up, and go enjoy doing anything that doesn’t involve switch configuration!
Q: I have a Cisco switch in my network, which I can access by hooking up a console cable directly to the device. I like to access the switch remotely using SSH. How can I enable ssh on my Cisco 3750 Catalyst Switch?
A: By default, when you configure a Cisco device, you have to use the console cable and connect directly to the system to access it. Follow the steps mentioned below, which will enable SSH access to your Cisco devices. Once you enable SSH, you can access it remotely using PuTTY or any other SSH client.
1. Setup Management IP
First, make sure you have performed basic network configurations on your switch. For example, assign default gateway, assign management ip-address, etc. If this is already done, skip to the next step.
In the following example, the management ip address is set as 192.168.101.2 in the 101 VLAN. The default gateway points to the firewall, which is 192.168.101.1
2. Set hostname and domain-name
Next, make sure the switch has a hostname and domain-name set properly.
3. Generate the RSA Keys
The switch or router should have RSA keys that it will use during the SSH process. So, generate these using crypto command as shown below.
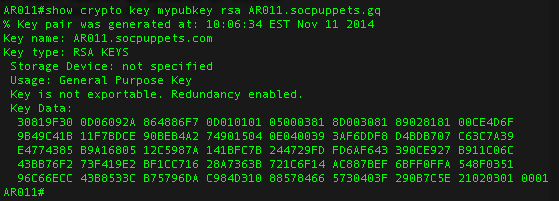
Also, if you are running on an older Cisco IOS image, it is highly recommended that you upgrade to latest Cisco IOS.
4. Setup the Line VTY configurations
Setup the following line vty configuration parameters, where input transport is set to SSH. Set the login to local, and password to 7.
If you have not set the console line yet, set it to the following values.
5. Create the username password
If you don’t have an username created already, do it as shown below.
Note: If you don’t have the enable password setup properly, do it now.
Make sure the password-encryption service is turned-on, which will encrypt the password, and when you do “sh run”, you’ll seee only the encrypted password and not clear-text password.
5. Verify SSH access
From the switch, if you do ‘sh ip ssh’, it will confirm that the SSH is enabled on this cisco device.
After the above configurations, login from a remote machine to verify that you can ssh to this cisco switch.
In this example, 192.168.101.2 is the management ip-address of the switch.
We currently have 355,864 full downloads including categories such as: software, movies, games, tv, adult movies, music, ebooks, apps and much more. Our members download database is updated on a daily basis.Take advantage of our limited time offer and gain access to unlimited downloads for FREE! That's how much we trust our unbeatable service. Zedload.com provides 24/7 fast download access to the most recent releases. Delta force xtreme 2 key generator.
If you enjoyed this article, you might also like.
Crypto Key Generate Modulus 1024 Cisco Switch For Windows 10
Next post: How to Backup Oracle Database using RMAN (with Examples)
Crypto Key Generate Modulus 1024 Cisco Switch Key
Previous post: How to Use C++ Single and Multiple Inheritance with an Example