Generate Rsa Private Key C
- Openssl Command To Generate Rsa Private Key
- Generate Rsa Private Key C Sheet Music
- Generate Rsa Key Linux
Chilkat • HOME • Android™ • Classic ASP • C • C++ • C# • Mono C# • .NET Core C# • C# UWP/WinRT • DataFlex • Delphi ActiveX • Delphi DLL • Visual FoxPro • Java • Lianja • MFC • Objective-C • Perl • PHP ActiveX • PHP Extension • PowerBuilder • PowerShell • PureBasic • CkPython • Chilkat2-Python • Ruby • SQL Server • Swift 2 • Swift 3/4 • Tcl • Unicode C • Unicode C++ • Visual Basic 6.0 • VB.NET • VB.NET UWP/WinRT • VBScript • Xojo Plugin • Node.js • Excel • Go
Adding your SSH key to the ssh-agent. Before adding a new SSH key to the ssh-agent to manage your keys, you should have checked for existing SSH keys and generated a new SSH key. When adding your SSH key to the agent, use the default macOS ssh-add command, and not an application installed by macports, homebrew, or some other external source. Before adding a new SSH key to the ssh-agent to manage your keys, you should have checked for existing SSH keys and generated a new SSH key. When adding your SSH key to the agent, use the default macOS ssh-add command, and not an application installed by macports. Why do we need SSH keys in git? SSH keys identify the user that is interacting with the git remote repository. I know it should be encrypting the connection but when uploading to GitHub, it means I am making my code public. Not necessarily, there are private repositories in GitHub. Also, there are other hosting providers as well. Why we need to generate ssh key in ubuntu. Dec 02, 2019 SSH keys come in many sizes, but a popular choice is RSA 2048-bit encryption, which is comparative to a 617 digit long password. On Windows systems, it is possible to generate your own SSH key pair by downloading and using an SSH client like PuTTY. On Mac® and Linux® systems, it is possible to generate an SSH key pair using a terminal window.
Openssl Command To Generate Rsa Private Key
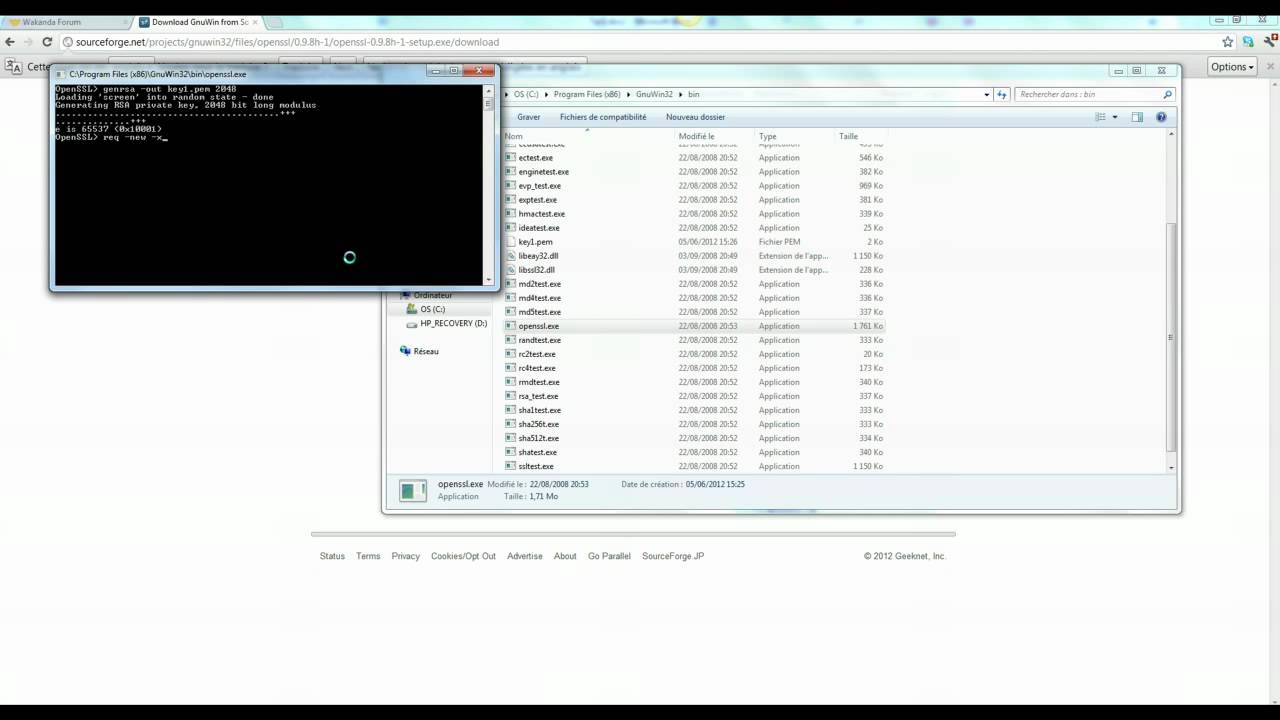
For the session opening, the client generates a 256-bits AES session key, and a 128-bits AES session IV (Initialisation Vector). The client sends a GSP SESSION INIT message to the server, encrypted with the client's RSA private key (that is, encrypted with the private key). Feb 04, 2012 The RSA (Rivest, Shamir, Adleman) encryption algorithm uses two Keys: Private and Public. Suppose Alice wants to send a message to Bob (for his eyes only!). She can encrypt the message using the RSA algorithm with Bob's Public Key, which is not a secret (that's why they call it Public). CkRsa rsa; // Generate a 1024-bit key. Chilkat RSA supports // key sizes ranging from 512 bits to 4096 bits. // Note: Starting in Chilkat v9.5.0.49, RSA key sizes can be up to 8192 bits. // It takes a considerable amount of time and processing power to generate // an 8192-bit key. Bool success = rsa. PKC is based on using special algorithms based on the mathematical concept of logarithms in order to generate two specific keys for a user. The private key is much like the key that you have to a building or a car. This key should belong only to you and can be used anywhere that has a matching keyhole. The public key is like the keyhole, as it. Public key in asymmetric cryptography is available to public but the private key must be protected with the user, else it can be used to decrypt data. In.NET, the RSACryptoServiceProvider and DSACryptoServiceProvider classes are used for asymmetric encryption. A random public/private key pair is generated when a new instance of the class is created.
| Office 2016 professional plus key generator. C++ example code showing how to generate an RSA public/private key.
| |||||
Generate Rsa Private Key C Sheet Music
© 2000-2020 Chilkat Software, Inc. All Rights Reserved.
