Ssh Generate Public Key Ubuntu
We’ll show you how to set up SSH keys on Ubuntu 16.04. SSH or Secure SHELL is the most popular and trusted UNIX-based cryptographic network protocol. It can be used for a secure data communication, remote server logins, remote command execution, and many other secure network services between two networked servers. Normally, password authentication is used to connect to a remote server via SSH but in this tutorial we will show you how to login to your Ubuntu 16.04 VPS using SSH keys. We will generate a key pair (private and public key), place the private key on your server and then use your locally stored private key to gain access to your server. This method provides a more secure way of connecting to your server, instead of just using a password.
- Ubuntu Ssh Public Key
- Ssh Generate Public Key Ubuntu Free
- Public Key Definition
- Generate Ssh Public Key
- Generate Public Ssh Key Windows
- Ssh Generate Public Key Ubuntu Free
Ssh-rsa AAAA./VqDjtS5 ubuntu@ubuntu For keys that were added to the SSH Agent (a program that runs in the background and avoids the need for re-entering the keyfile passphrase over and over again), you can use the ssh-add -L command to list the public keys for keys that were added to the agent (via ssh-add -l). This is useful when the SSH key is stored on a smart card (and access to the private key. Provide SSH public key when deploying a VM. To create a Linux VM that uses SSH keys for authentication, provide your SSH public key when creating the VM using the Azure portal, CLI, Resource Manager templates, or other methods. When using the portal, you enter the public key itself. To generate the keys, from a terminal prompt enter: ssh-keygen -t rsa This will generate the keys using the RSA Algorithm. During the process you will be prompted for a password. Simply hit Enter when prompted to create the key. By default the public key is saved in the file /.ssh/idrsa.pub, while /.ssh/idrsa is the private key. Jul 09, 2018 How to Add an SSH Public Key to GitHub from Ubuntu 18.04 LTS July 9, 2018 “How to Add an SSH Public Key to GitHub from an Ubuntu 18.04 LTS System” covers the entire process of creating an SSH key pair on an Ubuntu 18.04 LTS system and adding the public key to GitHub. Many Git servers authenticate using SSH public keys. In order to provide a public key, each user in your system must generate one if they don’t already have one. This process is similar across all operating systems. First, you should check to make sure you don’t already have a key. By default, a user’s SSH keys are stored in that user’s /.ssh directory. You can easily check to see if you have a key already by going. Jun 22, 2012 The DigitalOcean control panel allows you to add public keys to your new Droplets when they’re created. You can generate the SSH Key in a convenient location, such as the computer, and then upload the public key to the SSH key section. Then, when you create a new Droplet, you can choose to include that public key on the server. At this point, you have public and private keys that you can use to authenticate with your Ubuntu server. Step 3 – Copy the Public Key to the Ubuntu Server. Next, you will need to copy the public key from the client machine to your Ubuntu 18.04 server. You can copy the public key with ssh-copy-id utility as shown below: ssh-copy-id email.
During the course of this tutorial, we will also explain how to generate an SSH key pair on both Linux and a Windows operating system.
1. Generating SSH keys on Ubuntu 16.04
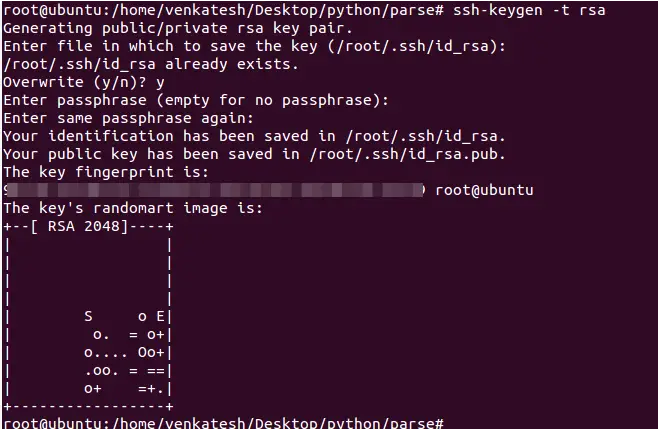
To generate the SSH key pair, simply run the following command from the terminal on your local Ubuntu 16.04 based computer:
You can just press Enter to leave the default values to all the questions. Optionally, you can also set a passphrase to add an extra layer of security, or just press Enter again if you don’t want to.
This will create a 2048 bit private and public key (id_rsa and id_rsa.pub) in the /root/.ssh/ directory on your local system.
Upload the Public Key to the Ubuntu 16.04 server with ssh-copy-id
The next step requires that you upload the generated public key to your remote Ubuntu server. There is more than one method to do this.
The most simple way is to use the ssh-copy-id utility. In order for this to work, you should be able to connect to your server via SSH using password authentication.
You can then use the following command to upload the public key to your remote server:
You will be asked to enter your user password (in our example that would be the root password) and press Enter. After the connection has been established, the contents of the id_rsa.pub (the public key) will be copied into the /root/ssh/authorized_keys file on the remote server.
The following output should be displayed:
From now on, you should now be able to authenticate to your Ubuntu server using your SSH keys.
Upload the Public Key to the Ubuntu server manually
If the ssh-copy-id tool is not available on your system, you can log in to your server and do this manually.
First, connect yo your server via SSH with:
Once connected, you will need to create a new .ssh directory on the remote server with the following command:
Next, you need to copy the public key into the authorized_keys file on the remote server. You can create and then add the contents of the public key using the nano text editor:
You will also need to open the SSH configuration file:
and make sure the following lines exist and are not commented:
Save the changes and restart the SSH service:
That’s it. From now on, you will be using the SSH keys every time you try to connect to your remote server.
Fifa 20 generator. I've done this before with them, so unless key is wrong, I don't think problem is on their end.
2. Generating SSH keys on Windows based system with PuTTY and PuTTYGen
If you are using Windows operating system on your local machine, then you will need PuTTY for connecting to your server via SSH and PuTTYgen to generate your SSH keys. You can download them over here (https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html).
To generate the SSH keys, go ahead and start PuTTYGen on your computer.
By using its best features, you can create an excellent report on your business as a professional. It will meet all the requirements of every type of business.You can also add and insert the pictures, charts, and graphs for your better understanding. Pirate bay.
At the bottom, you can choose the number of bits for your generated key. Type in 4096 and then click on Generate. Start moving your mouse around over the blank area on the PuTTYgen screen in order to generate a unique key based on your mouse movement input.
When the green progress bar fills in, the public key will be generated. You can copy they key and save it inside a .txt file on your computer.
To save the private key, you will need to click on the Save private key button. Additionally, you can also set a Key Passphrase for your private key.
Now you can open PuTTY and to assign the location of your private key, click on SSH under the Connection menu and then click on Auth. Click on the browse button and enter the location of your saved private key file.
Next, we need to upload the public key to your server. To do this, click on Session, enter your IP address and the SSH port number of your server, select SSH for Connection type and click on Open.
You will be asked for your user name and password. You can log in as user root, using your root password.
Once logged in to your server, first create the .ssh directory:
Then create the authorized_keys file inside the .ssh directory and add the contents of your public key inside this file:
You can also open the SSH configuration file on your server with:
and make sure that the following lines exist and are not commented:
If any changes have been made, dont forget to restart the sshd service with:
With this, the SSH keys has been succesfully configurad.You can now disconnect from your server and exit PuTTY. The next time your try to connect to your server, PuTTY will use the public key that you have set up in order to establish the connection.
3. Disable Password Authentication
Once you have successfuly configured the SSH keys using either of the above methods and you made sure that you can login to your server using SSH key based authentication, you can disable password based authentication to your server. This will add additional layer of security and will prevent all brute force attacks towards your server.
To disable the password-based authentication, open the SSH configuration file with:
Ubuntu Ssh Public Key
And uncomment the following line and set its value to “no”:
Restart the sshd service with:
Of course, you don’t have to set up the SSH key on your Ubuntu 16.04 VPS, if you use one of our Ubuntu Hosting services, in which case you can simply ask our expert Linux admins to set up the SSH keys for you. They are available 24×7 and will take care of your request immediately.
PS. If you liked this post please share it with your friends on the social networks using the buttons below or simply leave a comment in the comments section. Thanks.
-->With a secure shell (SSH) key pair, you can create a Linux virtual machine on Azure that defaults to using SSH keys for authentication, eliminating the need for passwords to sign in. VMs created with the Azure portal, Azure CLI, Resource Manager templates, or other tools can include your SSH public key as part of the deployment, which sets up SSH key authentication for SSH connections.
This article provides detailed background and steps to create and manage an SSH RSA public-private key file pair for SSH client connections. If you want quick commands, see How to create an SSH public-private key pair for Linux VMs in Azure.
For additional ways to generate and use SSH keys on a Windows computer, see How to use SSH keys with Windows on Azure.
Overview of SSH and keys
SSH is an encrypted connection protocol that allows secure sign-ins over unsecured connections. SSH is the default connection protocol for Linux VMs hosted in Azure. Although SSH itself provides an encrypted connection, using passwords with SSH connections still leaves the VM vulnerable to brute-force attacks or guessing of passwords. A more secure and preferred method of connecting to a VM using SSH is by using a public-private key pair, also known as SSH keys.
The public key is placed on your Linux VM, or any other service that you wish to use with public-key cryptography.
The private key remains on your local system. Protect this private key. Do not share it.
When you use an SSH client to connect to your Linux VM (which has the public key), the remote VM tests the client to make sure it possesses the private key. If the client has the private key, it's granted access to the VM.
Depending on your organization's security policies, you can reuse a single public-private key pair to access multiple Azure VMs and services. You do not need a separate pair of keys for each VM or service you wish to access.
Your public key can be shared with anyone, but only you (or your local security infrastructure) should possess your private key.
Private key passphrase
The SSH private key should have a very secure passphrase to safeguard it. This passphrase is just to access the private SSH key file and is not the user account password. When you add a passphrase to your SSH key, it encrypts the private key using 128-bit AES, so that the private key is useless without the passphrase to decrypt it. If an attacker stole your private key and that key did not have a passphrase, they would be able to use that private key to sign in to any servers that have the corresponding public key. If a private key is protected by a passphrase, it cannot be used by that attacker, providing an additional layer of security for your infrastructure on Azure.
Supported SSH key formats
Azure currently supports SSH protocol 2 (SSH-2) RSA public-private key pairs with a minimum length of 2048 bits. Other key formats such as ED25519 and ECDSA are not supported.
SSH keys use and benefits
When you create an Azure VM by specifying the public key, Azure copies the public key (in the .pub format) to the ~/.ssh/authorized_keys folder on the VM. SSH keys in ~/.ssh/authorized_keys are used to challenge the client to match the corresponding private key on an SSH connection. In an Azure Linux VM that uses SSH keys for authentication, Azure configures the SSHD server to not allow password sign-in, only SSH keys. Therefore, by creating an Azure Linux VM with SSH keys, you can help secure the VM deployment and save yourself the typical post-deployment configuration step of disabling passwords in the sshd_config file.
If you do not wish to use SSH keys, you can set up your Linux VM to use password authentication. If your VM is not exposed to the Internet, using passwords may be sufficient. However, you still need to manage your passwords for each Linux VM and maintain healthy password policies and practices, such as minimum password length and regular updates. Using SSH keys reduces the complexity of managing individual credentials across multiple VMs.
Generate keys with ssh-keygen
To create the keys, a preferred command is ssh-keygen, which is available with OpenSSH utilities in the Azure Cloud Shell, a macOS or Linux host, the Windows Subsystem for Linux, and other tools. ssh-keygen asks a series of questions and then writes a private key and a matching public key.
SSH keys are by default kept in the ~/.ssh directory. If you do not have a ~/.ssh directory, the ssh-keygen command creates it for you with the correct permissions.
Basic example
The following ssh-keygen command generates 2048-bit SSH RSA public and private key files by default in the ~/.ssh directory. If an SSH key pair exists in the current location, those files are overwritten.
Detailed example
The following example shows additional command options to create an SSH RSA key pair. If an SSH key pair exists in the current location, those files are overwritten.
Command explained
ssh-keygen = the program used to create the keys
-m PEM = format the key as PEM
-t rsa = type of key to create, in this case in the RSA format
-b 4096 = the number of bits in the key, in this case 4096
-C 'azureuser@myserver' = a comment appended to the end of the public key file to easily identify it. Normally an email address is used as the comment, but use whatever works best for your infrastructure.
-f ~/.ssh/mykeys/myprivatekey = the filename of the private key file, if you choose not to use the default name. A corresponding public key file appended with .pub is generated in the same directory. The directory must exist.
-N mypassphrase = an additional passphrase used to access the private key file.
Example of ssh-keygen
Saved key files
Enter file in which to save the key (/home/azureuser/.ssh/id_rsa): ~/.ssh/id_rsa
The key pair name for this article. Having a key pair named id_rsa is the default; some tools might expect the id_rsa private key file name, so having one is a good idea. The directory ~/.ssh/ is the default location for SSH key pairs and the SSH config file. If not specified with a full path, ssh-keygen creates the keys in the current working directory, not the default ~/.ssh.
List of the ~/.ssh directory
Key passphrase
Enter passphrase (empty for no passphrase):
It is strongly recommended to add a passphrase to your private key. Without a passphrase to protect the key file, anyone with the file can use it to sign in to any server that has the corresponding public key. Adding a passphrase offers more protection in case someone is able to gain access to your private key file, giving you time to change the keys.
Generate keys automatically during deployment
Ssh Generate Public Key Ubuntu Free
If you use the Azure CLI to create your VM, you can optionally generate SSH public and private key files by running the az vm create command with the --generate-ssh-keys option. The keys are stored in the ~/.ssh directory. Note that this command option does not overwrite keys if they already exist in that location.
Provide SSH public key when deploying a VM
To create a Linux VM that uses SSH keys for authentication, provide your SSH public key when creating the VM using the Azure portal, CLI, Resource Manager templates, or other methods. When using the portal, you enter the public key itself. If you use the Azure CLI to create your VM with an existing public key, specify the value or location of this public key by running the az vm create command with the --ssh-key-value option.
If you're not familiar with the format of an SSH public key, you can see your public key by running cat as follows, replacing ~/.ssh/id_rsa.pub with your own public key file location:
Output is similar to the following (here redacted):
If you copy and paste the contents of the public key file into the Azure portal or a Resource Manager template, make sure you don't copy any additional whitespace or introduce additional line breaks. For example, if you use macOS, you can pipe the public key file (by default, ~/.ssh/id_rsa.pub) to pbcopy to copy the contents (there are other Linux programs that do the same thing, such as xclip).
If you prefer to use a public key that is in a multiline format, you can generate an RFC4716 formatted key in a pem container from the public key you previously created.
To create a RFC4716 formatted key from an existing SSH public key:
SSH to your VM with an SSH client
With the public key deployed on your Azure VM, and the private key on your local system, SSH to your VM using the IP address or DNS name of your VM. Replace azureuser and myvm.westus.cloudapp.azure.com in the following command with the administrator user name and the fully qualified domain name (or IP address):
If you provided a passphrase when you created your key pair, enter the passphrase when prompted during the sign-in process. (The server is added to your ~/.ssh/known_hosts folder, and you won't be asked to connect again until the public key on your Azure VM changes or the server name is removed from ~/.ssh/known_hosts.)
Public Key Definition
If the VM is using the just-in-time access policy, you need to request access before you can connect to the VM. For more information about the just-in-time policy, see Manage virtual machine access using the just in time policy.
Use ssh-agent to store your private key passphrase
To avoid typing your private key file passphrase with every SSH sign-in, you can use ssh-agent to cache your private key file passphrase. If you are using a Mac, the macOS Keychain securely stores the private key passphrase when you invoke ssh-agent.
Verify and use ssh-agent and ssh-add to inform the SSH system about the key files so that you do not need to use the passphrase interactively.
Now add the private key to ssh-agent using the command ssh-add.
The private key passphrase is now stored in ssh-agent.
Use ssh-copy-id to copy the key to an existing VM
Generate Ssh Public Key
If you have already created a VM, you can install the new SSH public key to your Linux VM with a command similar to the following:
Generate Public Ssh Key Windows
Create and configure an SSH config file
You can create and configure an SSH config file (~/.ssh/config) to speed up log-ins and to optimize your SSH client behavior.
The following example shows a simple configuration that you can use to quickly sign in as a user to a specific VM using the default SSH private key.
Create the file
Edit the file to add the new SSH configuration
Example configuration
Add configuration settings appropriate for your host VM.
You can add configurations for additional hosts to enable each to use its own dedicated key pair. See SSH config file for more advanced configuration options.
Now that you have an SSH key pair and a configured SSH config file, you are able to sign in to your Linux VM quickly and securely. When you run the following command, SSH locates and loads any settings from the Host myvm block in the SSH config file.
The first time you sign in to a server using an SSH key, the command prompts you for the passphrase for that key file.
Next steps
Ssh Generate Public Key Ubuntu Free
Next up is to create Azure Linux VMs using the new SSH public key. Azure VMs that are created with an SSH public key as the sign-in are better secured than VMs created with the default sign-in method, passwords.